4 Silent Cybersecurity Threats Only CISM-Certified Pros Know How to Neutralize

In the high-stakes world of cybersecurity, the loudest threats—ransomware, phishing, DDoS attacks—grab headlines. But the most dangerous risks often lurk in the shadows, undetected until they cripple operations. These silent threats evade traditional security tools and exploit gaps in governance, making them favorites of sophisticated attackers.
Enter the CISM-certified information security manager—a professional trained not just to react to threats, but to dismantle them before they strike. Here are five stealthy dangers only CISM-certified pros are equipped to neutralize, and how Sprintzeal’s CISM Certification Training prepares you to turn them into opportunities.
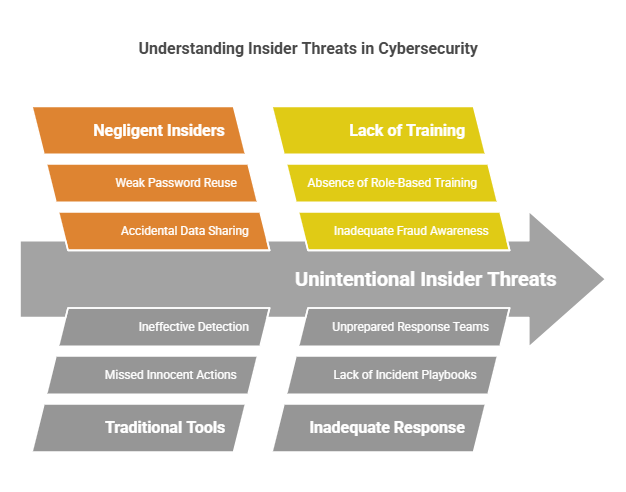
The Insider Enigma: Employees Who Don’t Know They’re a Threat
Real-World Example: A well-meaning finance employee at a healthcare firm emailed a spreadsheet of patient data to their personal Gmail to “work remotely.” The result? A HIPAA violation costing $1.2M in fines.
The Silent Risk:
- 68% of breaches involve negligent insiders (IBM X-Force).
- Traditional tools miss “innocent” actions like accidental data sharing or weak password reuse.
How CISM Neutralizes It:
CISM certification training teaches security governance frameworks to:
- Implement behavioral analytics that flag unusual data access patterns.
- Design role-based training (e.g., finance teams learn payment fraud red flags).
- Build incident response playbooks tailored to insider scenarios.
Sprintzeal’s Edge: Their CISM Boot Camp includes simulations where students contain a breach caused by a “trusted” insider.
Third-Party Time Bombs: Vendors with Hidden Backdoors
Real-World Example: In 2023, a major retailer’s POS system was hacked via a small HVAC vendor’s unpatched software. Losses: $8M.
The Silent Risk:
- 62% of breaches originate from third parties (Ponemon Institute).
- Most companies audit only 40% of vendors due to resource gaps.
How CISM Neutralizes It:
CISM-certified pros use risk management frameworks to:
- Create vendor risk tiers, prioritizing high-impact partners (e.g., cloud providers).
- Enforce contractual security clauses with breach penalties.
- Deploy continuous monitoring tools for real-time vendor threat detection.
Sprintzeal’s Edge: Their training includes a module on negotiating CCPA/GDPR compliance into vendor contracts.
Misconfigured Clouds: The Invisible Data Leak
Real-World Example: A tech startup left an AWS S3 bucket public, exposing 250GB of R&D data. Competitors capitalized within days.
The Silent Risk:
- 90% of cloud breaches stem from misconfigurations (Gartner).
- DevOps teams often prioritize speed over security, leaving gaps.
How CISM Neutralizes It:
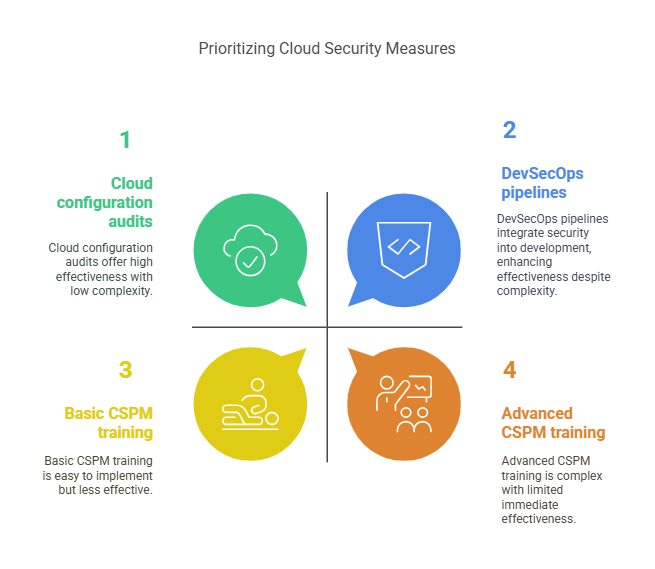
CISM-certified managers apply security architecture principles to:
- Automate cloud configuration audits using tools like AWS Config.
- Implement DevSecOps pipelines that bake security into CI/CD processes.
- Train engineers on cloud security posture management (CSPM).
Sprintzeal’s Edge: Their CISM Certification Training includes hands-on labs for securing multi-cloud environments.
AI-Powered Social Engineering: Phishing 2.0
Real-World Example: Attackers used AI-generated voice clones to mimic a CEO, tricking a CFO into wiring $2M to a fraudulent account.
The Silent Risk:
- AI-driven phishing attacks have spiked 135% in 2024 (Darktrace).
- Traditional email filters miss hyper-personalized deepfakes.
How CISM Neutralizes It:
CISM holders leverage incident management frameworks to:
- Deploy AI-powered threat detection that flags synthetic media.
- Conduct red team exercises simulating AI-driven attacks.
- Establish multi-factor authentication (MFA) protocols for financial transactions.
Sprintzeal’s Edge: Their program includes a workshop on countering generative AI threats.
Read Also: The Benefits of Energy-Efficient Doors for Your Home
Final Thought: In Cybersecurity, Silence Isn’t Golden—It’s Dangerous
CISM-certified professionals don’t just protect systems; they future-proof businesses. With silent threats evolving daily, the only wrong move is inaction. The question is: Will you be the hunter or the hunted?
Ready to become the threat hunter your organization needs?
Enroll in Sprintzeal’s CISM Certification Training Today




